The Cybersecurity Imperative
With the rapid growth and spread of data in the workplace, organizations face increasing challenges in terms of security. Bad actors have developed sophisticated methods for gaining access to your resources and stealing data, sabotaging your business, or extorting money. Every year, the number of attacks increases, and cybercriminals develop new methods of evading detection. For this reason, cybersecurity is an integral element that can make or break business. Implementing the right set of processes, best practices, and technology solutions that help protect your critical systems and network from digital attacks reduces the risk of business disruption, financial loss, and reputational damage from an attack.
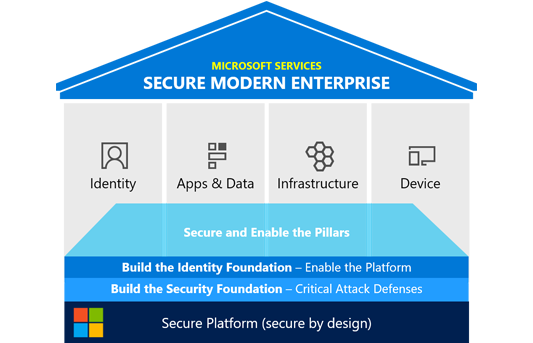
Securing Your Digital Transformation with Zero Trust
Instead of believing everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originated from an uncontrolled network. Regardless of where the request originates or what resource it accesses, the Zero Trust model teaches us to “never trust, always verify.” It is designed to adapt to the complexities of the modern environment that embraces the mobile workforce, protects people, devices, applications, and data wherever they are located.
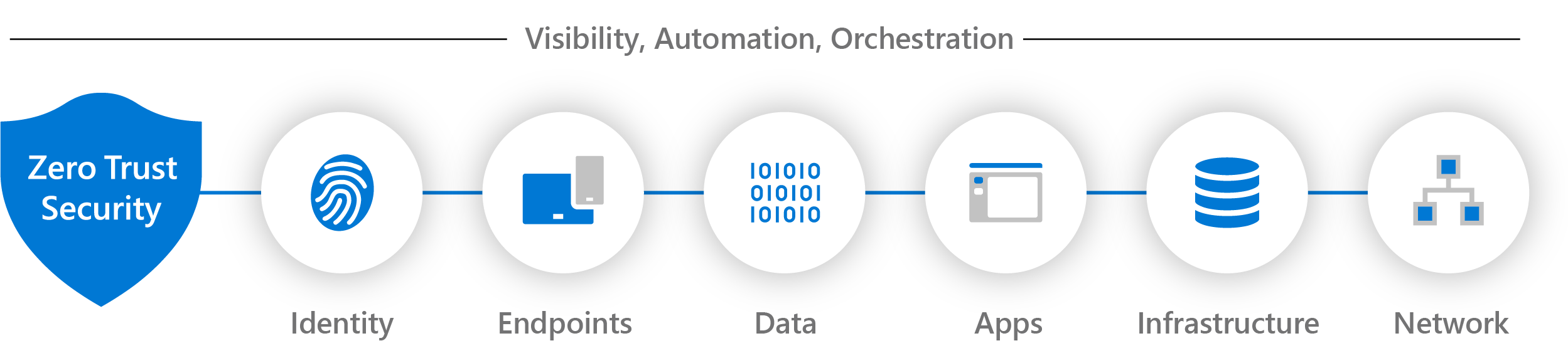
Your Zero Trust Solutions
Microsoft Entra ID (formerly Azure Active Directory)
Microsoft Entra ID Governance (formerly Microsoft Identity Governance)
Microsoft Sentinel
Multi-Factor Authentication
Conditional Access
Azure Key Vault
Microsoft Purview Information Protection
Microsoft Defender Suite
Microsoft Intune

How We Help You Fortify Your Modern Workplace




Choose Your Cybersecurity Weapons
One Cyberattack is One Too Many!
When it comes to cybercrimes, it is no longer a matter of “if” but “when” an attack will happen, especially if your company is not fully equipped with the right protection. At Cloud Ascent, we help you find the vulnerabilities in your organization and implement the necessary solutions to protect the identities, endpoints, apps, data, infrastructure, and networks in your environment.