In today’s digital age, where businesses rely on technology more than ever before, the importance of information security (i.e., infosec), particularly cybersecurity, cannot be overstated. As organizations continue to embrace digital transformation and technological progress, they are bound to face an ever-growing and evolving threat landscape.
In fact, the weakest link in your company’s cyber defenses is often not a vulnerability in your systems or software, but the human element – your employees.
That’s why raising cybersecurity awareness and providing comprehensive training to your employees is essential. With Microsoft Defender for Office 365’s Attack Simulation Training you can run realistic attack scenarios in your organization, identify vulnerable users, and drive behavior change through an integrated security awareness training program. These simulations not only help you train your employees to decrease their susceptibility to attacks, but also test your security policies and practices to fortify your defenses.

What are the requirements of using Defender for Office 365’s Attack Simulation Training?
You will need one of the following licenses to be able to benefit from the Attack Simulation Training
Office 365 E5 or Microsoft 365 E5.
Microsoft Defender for Office 365 Plan 2 or Microsoft 365 E5 Security add-on license.
Moreover, to manage and create attacks, you need one of the following roles which grants you permissions:
Global Administrator: this gives you global access to not only Attack Simulation Training, but also most management features and data across Microsoft online services.
Security Administrator: This role will give you access to all security features, not only Attack Simulation Training.
Attack Simulation Administrators: You can create and manage all aspects of attack simulation campaigns.
Attack Payload Author: You can create attack payloads that an admin can initiate later.
Types of Attack Simulations You can Run
1. Credential Harvest:
Users receive an email message with a URL that leads to a deceptive website that asks them for their username and password. Usually, the website’s page is designed with a theme that mimics a reputable website to establish trust with the user.
2. Malware Attachment:
Users receive an email with an attachment, and when they open it, malicious code runs on their device.
3. Link in Attachment:
This technique is a combination of credential harvest and malware attachment.
Users receive a message that contains a URL inside of an attachment. When they open the attachment and click on the URL, they’re taken to a website that asks them for their username and password.
4. Link to Malware:
Users receive a message with a link to an attachment on a reputable file-sharing platform like SharePoint Online or Dropbox. When the link is clicked, the attachment opens, enabling malicious code to run on the user’s device.
5. Drive-by-URL:
Users receive a message with a URL, and when clicked, it leads them to a website that runs background code aiming to gather information or execute malicious code on their device. Typically, the destination website is a reputable website that has been compromised or a clone of a well-known website. Familiarity with the website helps convince the user that the link is safe to click. This technique is also known as a watering hole attack.
6. OAuth Consent Grant:
An attacker creates a malicious Azure Application that seeks to gain access to data. The application sends an email request that contains a URL. When the recipient clicks on the URL, the consent grant mechanism of the application asks for access to the data (for example, the user’s Inbox).
The Landing Page
One of the components of the Attack Simulation Training is the landing page. It is the first thing users see when they fall prey to your phishing simulation. Below are the different landing page options you can choose from:
- Use Microsoft default landing page
Enables you to choose from Microsoft curated landing pages for a ‘click and go’ experience.
- Use a custom URL
Enables you to use in-house training assets through URL redirection.
- Create Your own landing page
Enables you to tailor the landing page to your requirements. For example, include your own branding, messaging, code, and more.
Attack Simulation Insights & Reports
Microsoft Defender for Office 365 Plan 2 offers insights and reports derived from simulation results and related training activities. These findings keep you updated on the threat readiness progress of your users and suggest actionable steps to better prepare them for future attacks.
In the Overview tab, you can find different insights and reports which include the following.
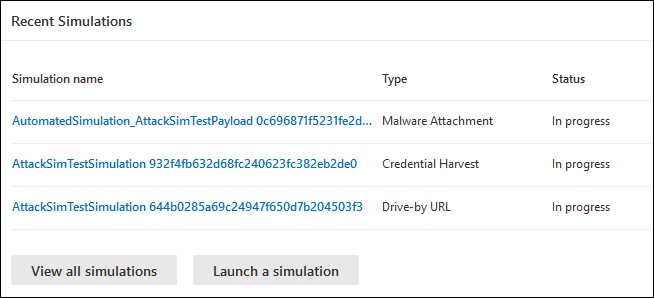
1. Recent Simulations Card
Microsoft Defender for Office 365 Plan 2 offers insights and reports derived from simulation results and related training activities. These findings keep you updated on the threat readiness progress of your users and suggest actionable steps to better prepare them for future attacks.
In the Overview tab, you can find different insights and reports which include the following.
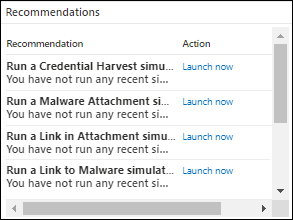
2. Recommendations Card
The recommendations card provides you with suggestions on different types of simulations to run in your organization.
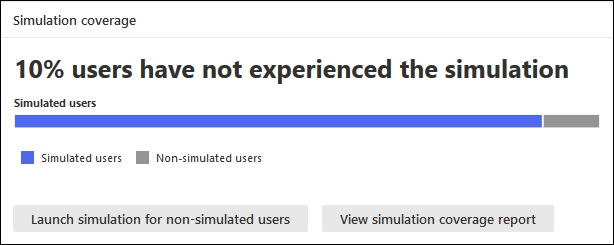
3. Simulation Coverage Card
Here you can see the percentage of users in your organization who have received a simulation (simulated users) in comparison to those who haven’t received a simulation (non-simulated users).
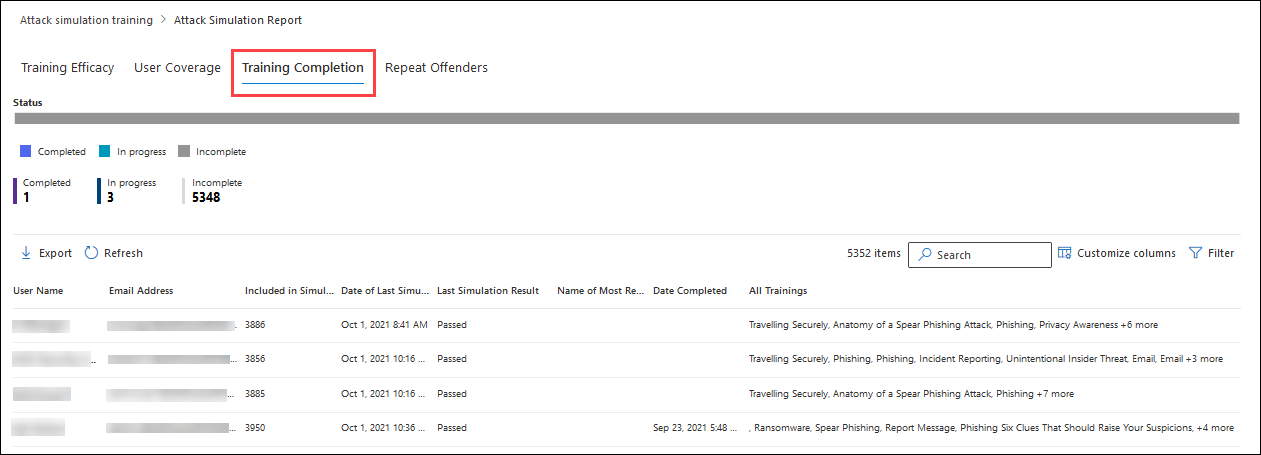
4. Training Completion Card & Report
The training completion card in the Overview tab categorizes the percentage of users who received trainings based on the following categories:
- Completed
- In progress
- Incomplete
To get more information on all trainings, you can go to the Training Completion tab where you will see a chart that shows the number of completed, in progress, and incomplete simulations. The chart also shows you all training details including the following information:
- Username
- Email address
- Included in simulation
- Date of last simulation
- Last simulation result
- Name of most recent training completed
- Date completed
- All trainings
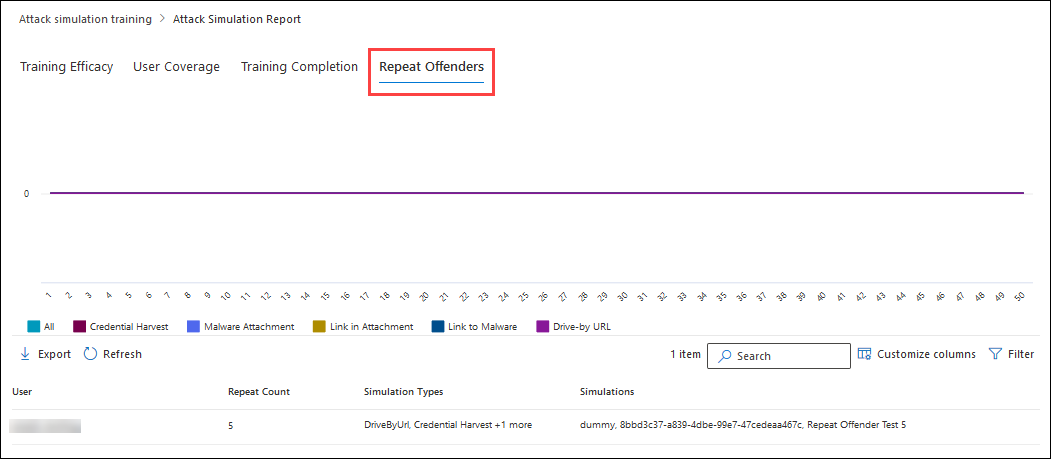
5. Repeat Offenders Card & Report
You get information about users who were compromised by consecutive simulations. The chart organizes repeat offender data by simulation type:
- All
- Malware Attachment
- Link to Malware
- Credential Harvest
- Link in attachments
- Drive-by URL
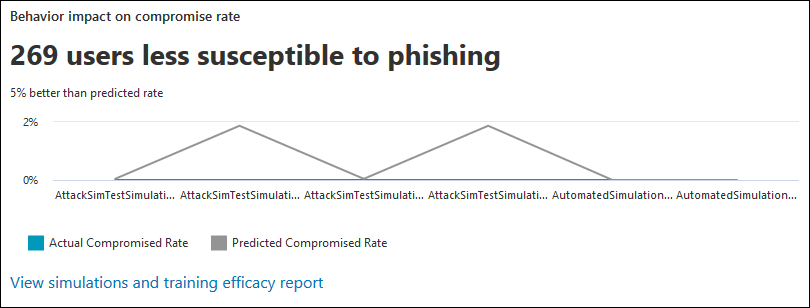
6. Behavior Impact on Compromise Rate Card
You get insights on how your users responded to your simulations as compared to the previous instances to track their progress. You can also run multiple simulations against the same group of users to check their level of cybersecurity awareness.
Tips on Running Microsoft Defender for Office 365’s Attack Simulation Training
One of the components of the Attack Simulation Training is the landing page. It is the first thing users see when they fall prey to your phishing simulation. Below are the different landing page options you can choose from:
- Use Microsoft default landing page
Enables you to choose from Microsoft curated landing pages for a ‘click and go’ experience.
- Use a custom URL
Enables you to use in-house training assets through URL redirection.
- Create Your own landing page
Enables you to tailor the landing page to your requirements. For example, include your own branding, messaging, code, and more.
Conclusion
In today’s data-driven world, businesses can no longer afford to overlook the necessity of investing in cybersecurity, as losing valuable data to hackers is a risk they cannot bear. For this reason, one of the most important steps to prevent cyberattacks is by training employees and raising their cybersecurity awareness, as human error is a leading cause of security breaches.
Microsoft Defender for Office 365’s Attack Simulation Training is a comprehensive cybersecurity solution aimed at strengthening your organization’s security posture. Through realistic attack simulations, it empowers businesses to evaluate and enhance their defenses by identifying vulnerabilities and educating users about potential threats. This tool not only raises cybersecurity awareness, but also provides valuable insights and reports to track progress, ensuring a more resilient and secure workplace.
Contact us to learn more about Microsoft Defender for Office 365 Plan 2 and see how we can help you strengthen your company’s security.





