Microsoft Defender Antivirus and Microsoft Defender for Endpoint Defined
Microsoft Defender Antivirus, formerly known as Windows Defender, is an antivirus software that is built into Windows 10, 11, and versions of Windows Server. It protects your device from viruses, malware, and other threats by scanning, detecting, and removing most of the threats that jeopardize your operating system.
While Microsoft Defender Antivirus is a built-in software program designed to protect a single device, Microsoft Defender for Endpoint, formerly known as Microsoft Defender Advanced Threat Protection, is an enterprise endpoint security platform designed to protect enterprise networks; it prevents, detects, investigates, and responds to advanced threats across all devices in your environment. Defender for Endpoint offers many security layers including core Defender Vulnerability Management, Attack Surface Reduction, Next-generation Protection, Endpoint Detection and Response (EDR), and Automated Investigation and Remediation.

Even though Microsoft Defender Antivirus works with non-Microsoft antivirus/antimalware products, it is the most compatible with Microsoft Defender for Endpoint. Combined with Defender for Endpoint capabilities, such as Endpoint Detection and Response and Automated Investigation and Remediation, you get better protection that’s coordinated across products and services. Below are some of the important features you get when you use both security products together.
Advantages of Using Microsoft Defender Antivirus and Microsoft Defender for Endpoint Together
- Antivirus Signal Sharing
Together, Microsoft Defender Antivirus and Microsoft Defender for Endpoint offer a single robust platform that receives signals from both security solutions. This is because Microsoft applications and services share signals across your enterprise organization.

- Threat Analytics and Your Score for Devices
Microsoft Defender Antivirus gathers underlying system data and shares them with Microsoft Defender for Endpoint. The data is instantly used by threat analytics and Microsoft Secure Score for Devices capabilities to provide your organization with more meaningful security information, such as recommendations and opportunities to improve your organization’s security posture.

- Network Devices
Network protection is an Attack Surface Reduction capability, included in Microsoft Defender for Endpoint, that protects organizations by preventing employees from accessing dangerous domains that may host phishing, scams, exploits, and other malicious content on the internet. By default, network protection safeguards your devices from known malicious IP addresses and URLs using the SmartScreen feed. You can also block specific IP addresses and URLs that might put your organization at risk. However, in order to enable network protection, Microsoft Defender Antivirus needs to be active.
- Tamper Protection
During certain types of cyberattacks, hackers infiltrate your environment through disabling security features, such as antivirus protection, on your machines. This gives them easier access to your data to install malware or exploit your identity and devices. However, if you are using Microsoft Defender Antivirus in your environment, you can enable tamper protection through Microsoft Defender for Endpoint or Microsoft Intune to prevent hackers from disabling your local security settings. With tamper protection, Microsoft Defender Antivirus will be locked—preventing your security settings from being changed.
- File Blocking
When an attack occurs in your organization, one of the first important steps to take is to contain it by stopping the malicious process and quarantining the file where it was observed. When used together, Microsoft Defender Antivirus and Microsoft Defender for Endpoint enable you to stop and quarantine the infected files across all devices in your organization. The “Stop and Quarantine File” action includes stopping running processes, quarantining the files, and deleting persistent data such as registry keys. This action takes effect on devices with Windows 10, version 1703 or later, and Windows 11 and Server 2012 R2+, where the affected file was observed in the last 30 days. After an attack, once you have determined that the file is clean again, you can restore it from quarantine at any time.

How to Onboard Defender for Endpoint on Windows Devices
You can choose one of the following options to onboard your company’s Windows devices to Microsoft Defender for Endpoint:
- Local script (for onboarding devices manually in the Microsoft 365 Defender portal)
Local scripting is for evaluation purposes and is not normally used in production deployments. For this reason, there are concerns about environmental impact, so Microsoft recommends limiting the number of deployments using local scripts to ten devices. If you are deploying to a production environment, it is best to use other deployment options which will be listed below. The steps to onboard Defender for Endpoint using this method are simple. First, you need to open the configuration page .zip file that you downloaded from the service onboarding wizard or from the Microsoft 365 Defender portal and in the navigation pane, go to settings -> Endpoints-> Device->Management-> Onboarding. Then, select Windows 10 or 11 as operating systems and local script as the deployment method and download the package.
- Group Policy (if you’re already using Group Policy in your organization)
To onboard windows devices using group policy, follow the same steps as local scripting, but in the deployment method, you need to choose group policy.
- Microsoft Intune (if you’re already using Intune)
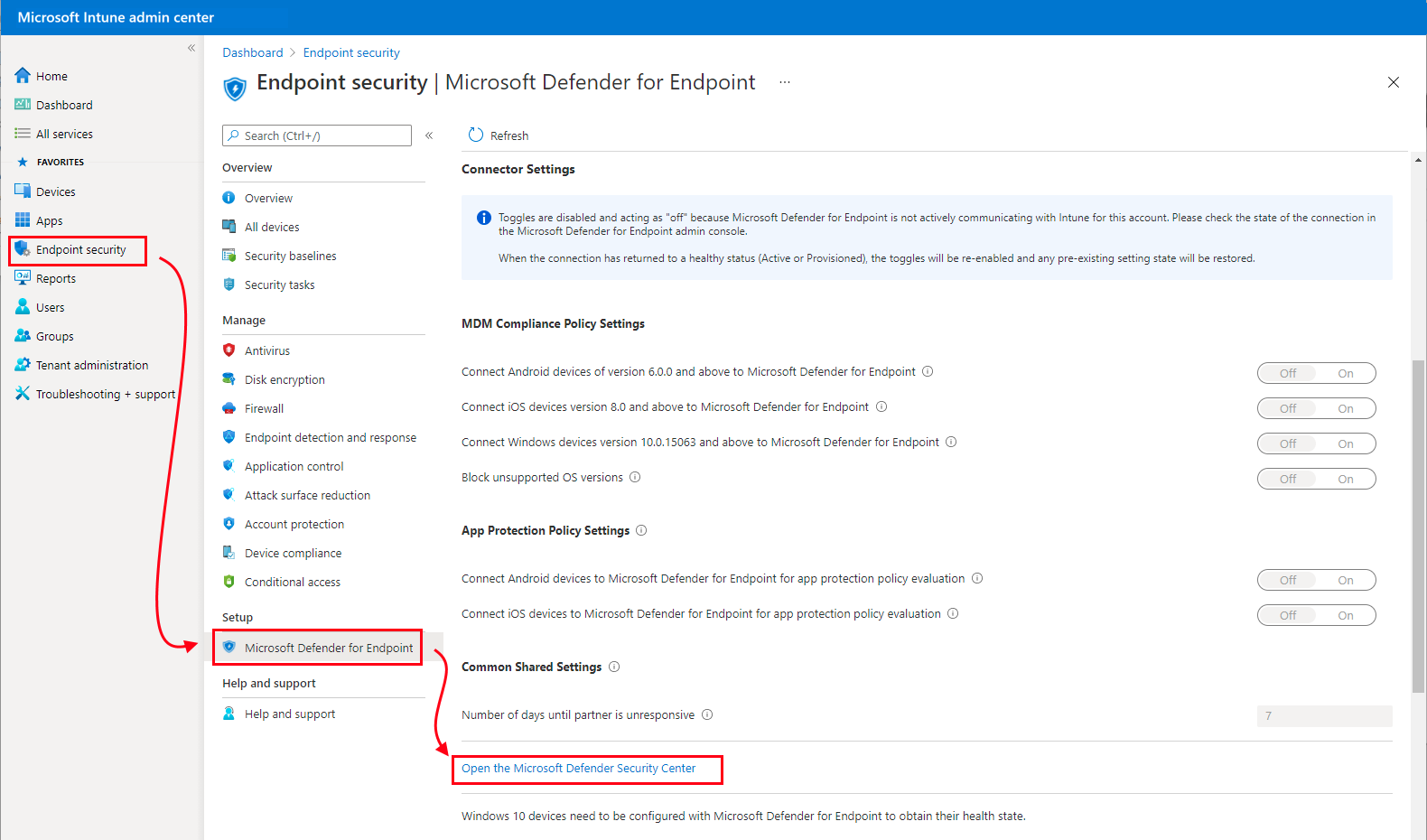
As Microsoft Defender for Endpoint integrates seamlessly into Intune, you only need to activate this integration through setting up the service-to-service connection between Intune and Microsoft Defender for Endpoint. This requires administrative access to both the Microsoft Defender Security Center and to Intune. To enable Microsoft Defender for Endpoint, you need to sign in to the Microsoft Intune admin center, select Endpoint Security->Microsoft Defender for Endpoint under Setup, and then select Open the Microsoft Defender Security Center.
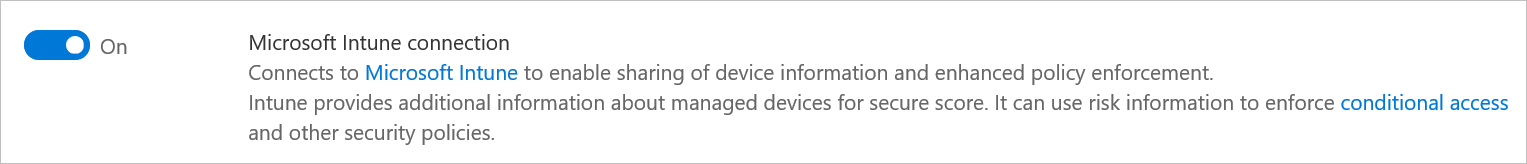
In Microsoft 365 Defender, (previously the Microsoft Defender Security Center), select Settings-> Endpoints-> Advanced features and turn on the Microsoft Intune connection.
- Microsoft Endpoint Configuration Manager
Go to https://security.microsoft.com, select Settings -> Endpoints, under Device Management Onboarding, select the OS option as Windows 10 and 11 and the deployment method as Microsoft Endpoint Configuration Manager. Then, click on download onboarding package and save it in your device. After that, go to the Microsoft Endpoint Configuration Manager console, go to Assets and Compliance -> Endpoint Protection -> Microsoft Defender for Endpoint Policies and complete the Name and Description and the Policy type as Onboarding. Then, browse and upload the previously downloaded onboarding package from MDE and complete the policy creation. Once completed, you need to deploy the policy creation to a device collection and then you would be ready to go.




